
All computer hardware and software have a product lifecycle. There are many risks of using old and outdated software and hardware. Knowing the risks can help you decide when to upgrade and what might happen if you choose not to.
End of Support
‘End of support’ is the expiry date for products. It happens when products are no longer supported by their developer and will no longer receive security updates or technical support. In most cases, products will continue to work after the end of the support date. However, you will be more open to increased cyber security risks.
Cyber Risks
The risk of a cyber security incident significantly increases when you use unsupported products. Cybercriminals know some users still use products that are ‘End of Support’. They are opportunistic and are happy to break into a system with a new “Zero Day” vulnerability as they are with a vulnerability from 2010.
Ransomware Targets
Unpatched vulnerabilities remain the most prominent attack vectors exploited by ransomware groups. The Ryuk, Conti and Netwalker ransomware all use vulnerabilities in older versions of Adobe Acrobat to exploit and infect their targets.
The Reveton ransomware uses vulnerabilities in Oracle Java, which were patched in 2012 and 2013 by Oracle. Still, due to many businesses’ poor patching and upgrade practices, they find themselves vulnerable to attack in 2022.
Corum Cyber Defence observes attacks such as this regularly. We recently detected attackers using a vulnerability in Microsoft Office from 2017, allowing attackers to hijack Microsoft Word or Microsoft Excel to execute malicious code.

What about Windows 7 (and 8)?
Windows 7 is an easy target of ransomware. It has been since before ransomware was as prevalent as it is today. The WannaCry ransomware appeared in May 2017, starting with a massive attack on vulnerable SMB services targeting Windows XP and Windows 7 systems. The ransomware infected over 300,000 computers in over 150 countries. WannaCry was the biggest ransomware outbreak in history and caused the world to take notice of ransomware.
Pharmacy Security is like an Onion
When you think about security for your pharmacy, imagine an onion. Your pharmacy needs to have a layered defence. Any weak spots in your defence will allow the attacker to access your network and your other systems.
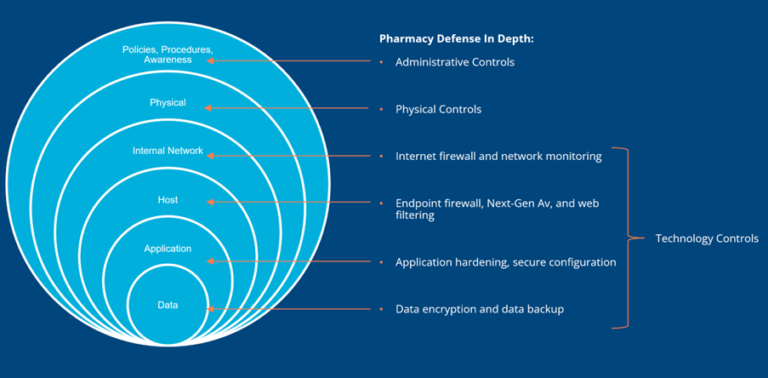
If attackers can get access through an unpatched vulnerability in Microsoft word, or an old POS system running Windows 7, they will. They are opportunistic and will use that weak system as a stepping stone to finding the other weaknesses in your pharmacy network.
Perhaps they find you use the same password on all other systems in the pharmacy or that you keep your passwords for your banking in a text file in your documents.
They will continue to find vulnerabilities in your defences to gain further access to your business and your personal life and finances. They will only stop when they get to the money, be it your bank, accounts, or a ransomware demand.
If you are worried about the security of your pharmacy systems and want to know how you can keep abreast of vulnerabilities in your pharmacy and protect yourself from ransomware, speak to your Customer Success Manager or contact us on 1300 669 865.


