Did you know that application control technologies can help stop the execution of malware?
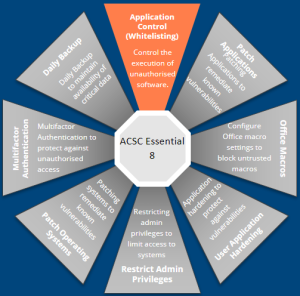
Application control, sometimes called application whitelisting, is a security approach designed to protect against malicious code (also known as malware) executing on systems. Application control technologies are intended to stop the execution of malware and other unauthorised software.
Application control technologies are often more effective at stopping unknown malware threats than conventional antivirus software and other traditional antimalware security controls. Unlike traditional antivirus software, which blocks known bad activity, application control technologies are designed to permit known good activity and block all other.
When implemented correctly, it ensures that only approved applications can be executed. This is important because today’s malware threats are increasingly customised and targeted, making traditional detection technologies largely ineffective.
In addition to preventing the execution of unapproved applications, application control can contribute to the identification of attempts by a threat actor to execute malicious code on the system, preventing attackers from gaining a hold of the system.
Application control system can be based on monitoring and controlling a variety of application file and folder attributes, including the following:
File path. This is the most general attribute: permitting all applications within a particular path (directory/folder).
Filename. The name of an application file is too general to be used on its own and often is used in conjunction with other attributes.
File size. This attribute is typically used only in combination with other attributes, such as filename.
Digital signature or publisher. A digital signature provides a reliable, unique value for an application file that the recipient verifies to ensure that the file is legitimate and has not been altered.
Cryptographic hash. A cryptographic hash provides a reliable, unique value for an application that can detect minor changes to a file. Cryptographic hashes are accurate no matter where the file is placed, what it is named, or how it is signed.
When implemented in its most restrictive state, application control does not work well in small organisations with limited IT staff. It can prevent application upgrades and, in worse cases, stop systems from operating.
Corum’s recommended approach for implementing Application Control in a Pharmacy is to utilise a cloud-based solution that combines some of the above attributes. We recommend a focus on protecting critical operating system components and blocking executables and other files unless they meet age or prevalence rules or are trusted applications such as Microsoft Office and Pharmacy programs. This approach strikes a balance and, when combined with the other Essential 8 Controls, provides a strong defence from threat actors.
If you are worried about the security of your pharmacy systems and want to know how you can keep abreast of vulnerabilities in your pharmacy and protect yourself from ransomware, speak to your Customer Success Manager or contact us on 1300 669 865.
