Did You Know that Patching Applications is Not the Same as Patching Operating Systems?
It’s critical to update your applications whenever possible. Patching applications prevent threat actors from using known security vulnerabilities to breach your network and achieve their objectives.
Patching Applications is not the same as Patching Operating Systems
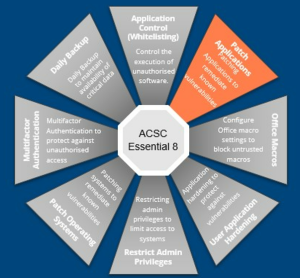
First, patching applications is not the same process as patching operating systems. Patching applications is about applying updates and fixes to the programs you use day in, day out. Examples include your dispensing and point of sales applications, web browsers such as Chrome or Mozilla, and document programs like Adobe PDF reader and the Microsoft Office suite.
According to the Australian Cybersecurity Centre (ACSC), once a patch for an application is released by a vendor, the patch should be applied in a timeframe commensurate with an organisation’s exposure to the security vulnerability and the level of cyber threat the organisation is aiming to protect themselves against.
For example, a vulnerability is discovered for Google Chrome that allows a threat actor to take control of it remotely. It can be expected that adversaries will develop malicious code within 48 hours. In fact, there are cases in which threat actors have developed malicious code within hours of newly discovered security vulnerabilities. Within your pharmacy, you are using Chrome from the moment your store opens till the time you close. To ensure your business is protected, you must apply a patch to Google Chrome within the next 48 hours to minimise your risks. Ideally, applying the patch earlier is better.
Understanding Vulnerability Ratings
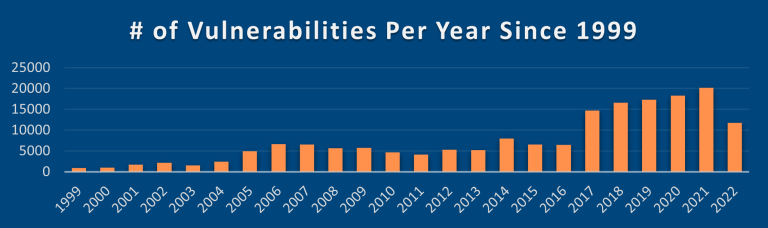
Due to the huge number of vulnerabilities that are discovered, a Common Vulnerability Scoring System (CVSS) was developed to help developers and security professionals assess the threat levels of vulnerabilities and prioritise applying patches and fixes.
Did you know that the number of vulnerabilities discovered increases every year? Whenever a security vulnerability is discovered, it is assigned a vulnerability rating score. The vulnerability scores and other details are published in open databases. Each is assigned a CVSS score which includes a criticality rating.
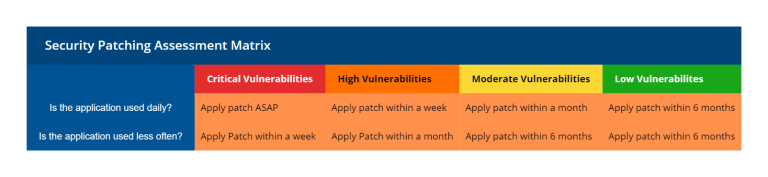
Patching Based on Risk
To use the CVSS scores, you don’t need to understand the vulnerability in detail or how the vulnerability can be exploited. As a business owner, all you need to know is the criticality rating of the vulnerability and apply patches accordingly. Corum recommends adopting the following application patching methodology within your pharmacy
Risks of Applying Vs Not Applying
When patching, you may be concerned about the risk of patches breaking applications or operating systems and the associated outage this may cause. Corum recommends accounting for faults during patching by establishing clear patch management processes. In doing so, you can follow a strict process to test the patch in a limited way, say on a spare or back-office machine, before installing it on your critical dispense and point of sale.
When you have limited resources or are constrained by time, you should prioritise the deployment of patches. For example, patches should first be applied to any internet-facing services. Then, after testing, apply the patch to your critical machines that would be a target of a threat actor. (Think computers with customer information, banking details and sensitive personal data). Then when time permits, apply to the rest of your machines.
Threat actors will often target low-hanging fruit, the vulnerabilities that are easy to exploit and are widely available. Running unpatched web browsers, office programs and PDF readers are seen as being widely available. When there is a vulnerability with working exploit code (known as a Zero-day) they will rush to exploit it before a patch is released. Thankfully, in most cases, the vendor will release patches before there is working exploit code, and when the patch is critical, you need to patch asap. Not applying patches increase your risk of compromise or ransomware-type event.
If you are worried about the security of your pharmacy systems and want to know how you can keep abreast of vulnerabilities in your pharmacy and protect yourself from ransomware, speak to your Customer Success Manager or contact us on 1300 669 865.
